Growth of Big Data Requires Android Users to Have VPNs
Smart Data Collective
JANUARY 6, 2025
Android users should take advantage of VPNs to safeguard their data from hackers, the government and big tech.

Smart Data Collective
JANUARY 6, 2025
Android users should take advantage of VPNs to safeguard their data from hackers, the government and big tech.

Smart Data Collective
NOVEMBER 20, 2022
For example, healthcare providers who handle sensitive patient data require data centers that are explicitly HIPAA-compliant. PCI-DSS compliance, on the other hand, is required for any organization that handles the transfer of credit card details.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Astera
MAY 25, 2023
Big Data Security: Protecting Your Valuable Assets In today’s digital age, we generate an unprecedented amount of data every day through our interactions with various technologies. The sheer volume, velocity, and variety of big data make it difficult to manage and extract meaningful insights from.

Smart Data Collective
APRIL 15, 2020
Big Data Requires Greater Prudence with File Sharing. Big data advances are changing the art of file sharing. Your data is gold. In many cases, depending on your permissions, P2P users may gain access to all your files. It is one of the easiest ways for malware attacks.
Analysts Corner
OCTOBER 26, 2023
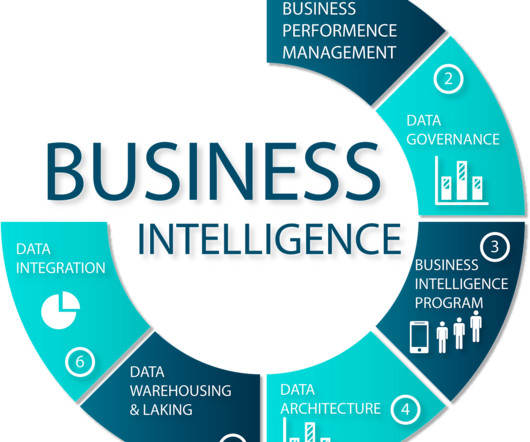
Customization and Flexibility: Select BI tools that offer customization and flexibility, enabling your organization to tailor the BI system to its unique needs and requirements.

Domo
MAY 30, 2024
This should include not only permissions but also tracking who accessed what data and when, to keep your organization accountable and compliant with data protection regulations. Celebrating these contributions can boost morale and encourage a proactive approach to data management.
ElegantJ BI
SEPTEMBER 30, 2021
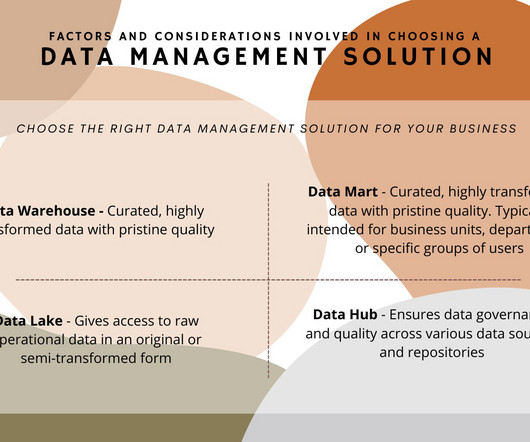
Suitable For: Use by business units, departments or specific roles within the organization that have a need to analyze and report and require high quality data and good performance. Advantages: Can provide secured access to data required by certain team members and business units.
Let's personalize your content