Scaling Data Access Governance
Dataversity
OCTOBER 4, 2022
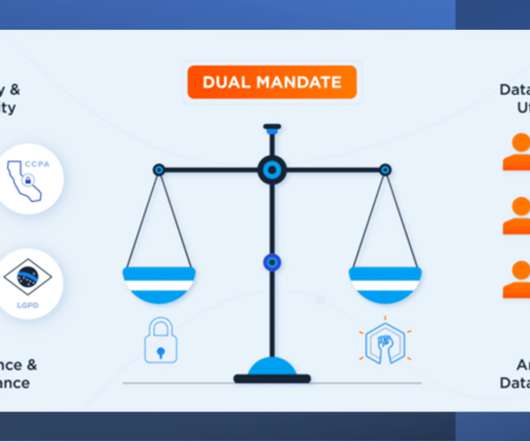
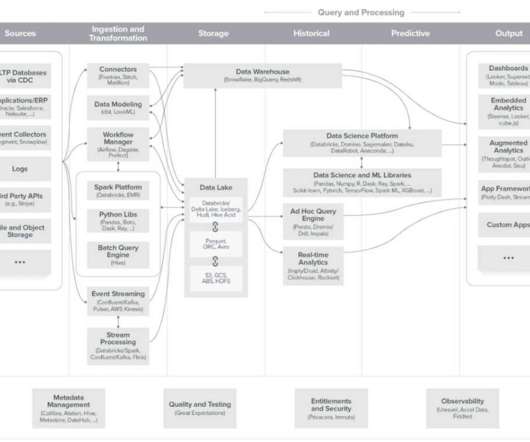
The rise of data lakes and adjacent patterns such as the data lakehouse has given data teams increased agility and the ability to leverage major amounts of data. Constantly evolving data privacy legislation and the impact of major cybersecurity breaches has led to the call for responsible data […].















Let's personalize your content