8 Crucial Tips to Help SMEs Guard Against Data Breaches
Smart Data Collective
MAY 25, 2023
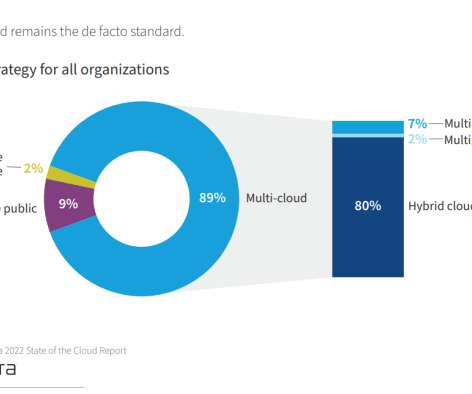
Additionally, it’s important for small businesses to have a comprehensive cybersecurity plan in place in order to identify potential threats and respond quickly if a breach does occur. A cybersecurity strategy is essential for protecting employees, corporate, and customers’ confidential data.







Let's personalize your content